In this edition
Azure Architect Tip of the Day
Use Private DNS Resolver to Eliminate Custom DNS Servers in Hybrid Setups
Many architectures still deploy custom DNS forwarder VMs, maintain BIND/Windows DNS servers, or build complex split-brain DNS setups just to make on-prem and Azure workloads resolve each other.
In 2025, this is unnecessary complexity.
Azure Private DNS Resolver gives you a fully managed, highly available DNS forwarding service without VMs, patching, or manual zone management.
What it enables:
Seamless name resolution between on-prem and Azure
Clean integration with Private Endpoints
Outbound forwarding rules to your on-prem DNS
Inbound endpoints for on-prem → Azure resolution
Zero maintenance (no VMs, no updates, no failover planning)
Why it matters:
Hybrid DNS is one of the top hidden sources of outages: broken forwarders, stale records, mismatched zones, or failed DNS VMs.
Private DNS Resolver removes that operational burden entirely, making DNS resolution consistent, centralized, and resilient across your Landing Zone.
Architect’s takeaway:
Treat Private DNS Resolver as your default DNS architecture whenever hybrid connectivity or Private Endpoints are in play. It simplifies network design and significantly improves reliability.
Azure Good-Reads
Top 5 Azure Governance Mistakes I’ve Seen in Enterprises (and How to Avoid Them)
Introduction: Governance Is the First Thing Everyone Skips - and the First Thing They Regret
In my 25+ years in IT and cloud architecture - and having worked on large-scale Azure migrations, enterprise landing zones, and cloud modernization programs - I have noticed a pattern:
Most governance failures aren’t caused by lack of knowledge but by rushing to build before setting guardrails.
Enterprises often begin their Azure journey with excitement: subscriptions get created, workloads spin up, data flows in. And before long, cost overruns, policy violations, and security exposures start creeping in. Governance becomes a patchwork effort rather than a strategic foundation.
Here are the five most common Azure governance mistakes I’ve seen firsthand, why they happen, and how to fix them before they cost your organization money, security, and peace of mind.
1. Weak Management Group and Subscription Design
The mistake:
Treating Azure subscriptions like folders - spinning them up ad hoc without a design or hierarchy.
Real-world example:
A financial services client once had 60+ subscriptions created over two years by different teams. There was no management group structure, and policies were applied inconsistently. When we tried to apply an “Allowed Locations” policy globally, we found dozens of workloads running in regions outside compliance scope. Cleaning that up took months.
Why it matters:
Without a proper management group structure, you can’t enforce policies, apply RBAC consistently, or segregate production and non-production workloads.
How to fix it:
Design a management group hierarchy early (Below is just an example)
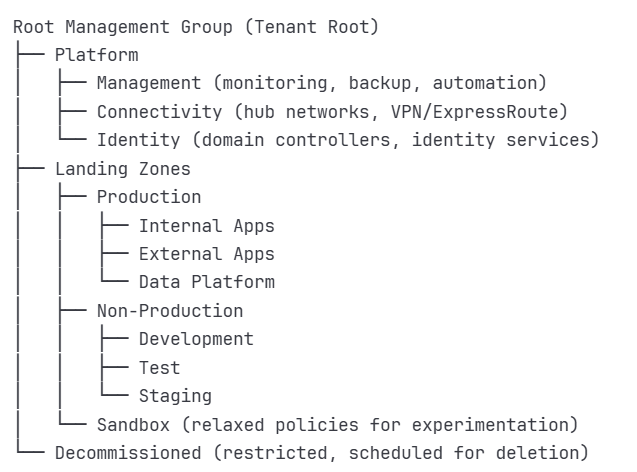
Use IaC to standardize deployments.
Apply Azure Policy and RBAC at the management group level so governance cascades automatically.
Pro tip: Always treat the “Root Management Group” as your control plane. That’s where your compliance, region restrictions, and baseline guardrails belong.
2. Over-Permissive RBAC and Access Sprawl
The mistake:
Everyone’s an Owner. It feels convenient - until it’s catastrophic.
Real-world example:
At one enterprise, a developer had Owner access in a shared subscription. During a maintenance task, they accidentally deleted a resource group containing a staging environment used for testing an upcoming release. There was no soft delete or backup configured for some assets. The loss delayed the release by two weeks.
Why it matters:
Over-permissioning increases the attack surface and operational risk. Azure AD identities - human or service - must follow the principle of least privilege.
How to fix it:
Use role-based access control (RBAC) scoped to the lowest necessary level (resource or resource group).
Implement Azure Privileged Identity Management (PIM) for Just-in-Time (JIT) elevation.
Regularly review access and remove unused role assignments.
Require MFA for all accounts with elevated privileges.
Pro tip: Nobody - not even admins - should hold permanent “Owner” rights. You can always request temporary elevation through PIM when needed.
3. Ignoring Azure Policy and Compliance Guardrails
The mistake:
Treating Azure Policy as optional - or only enabling it after a compliance breach.
Real-world example:
A healthcare customer discovered that nearly 30% of their Azure Storage Accounts were unencrypted because encryption-at-rest had never been enforced. Worse, resources had inconsistent tags, so they couldn’t identify data owners. It only came to light during a compliance audit.
Why it matters:
Azure Policy is your safety net. It ensures consistency, enforces standards, and automates compliance. Without it, every team does things “their way,” and governance becomes impossible.
How to fix it:
Create policy initiatives for key governance areas: allowed regions, required tags, enforced encryption, SKU restrictions, etc.
Apply them at management group or subscription level for full coverage.
Use remediation tasks to auto-fix non-compliant resources.
Treat policy as code - version it, test it, and deploy it via CI/CD pipelines.
Pro tip: Combine Policy with Microsoft Defender for Cloud (MDC) recommendations for proactive compliance insights.
4. Poor Cost Governance and Lack of Accountability
The mistake:
Assuming “FinOps will handle it later.” By the time they notice, the invoice has already arrived.
Real-world example:
During a seasonal sales campaign, a retail client’s auto-scaling app service farm expanded aggressively due to a traffic spike. There were no budgets, alerts, or cost limits configured. Their monthly Azure bill jumped from $70K to $125K overnight - and nobody knew until accounting flagged it.
Why it matters:
Without budget controls, tagging, and visibility, Azure can become a black hole of untracked spending. Cost overruns are governance failures - not billing surprises.
How to fix it:
Set budgets and alerts in Azure Cost Management for each subscription and resource group.
Tag all resources with
CostCenter,Environment, andOwner.Automate shutdowns for dev/test environments during off-hours.
Review Cost Analysis dashboards weekly and deallocate idle resources.
For predictable workloads, use Reserved Instances or Savings Plans.
Pro tip: Publish a monthly “Cloud Spend Report” - it creates transparency and accountability across teams.
5. Inconsistent Naming and Tagging Standards
The mistake:
Every team uses its own naming convention (or none). You can’t manage what you can’t identify.
Real-world example:
A large enterprise I worked with had over 5,000 resources. Some were named like vm01, others like prod-web-eastus, and others were completely random. When a security alert came in for a VM, it took hours to identify who owned it. During incidents, such confusion is costly.
Why it matters:
Standardized names and tags make governance, cost allocation, and automation manageable at scale. Inconsistent naming is one of the top causes of operational friction in Azure.
How to fix it:
Define a naming convention (e.g.,
{resource-type}-{app/workload}-{environment}-{region}-{instance}).Examples:
rg-salesapp-prod-eastus-01sqldb-salesapp-prod-eastus-primaryapp-salesapp-prod-eastus-01stsalesappprodeastus01 (storage accounts: no dashes, 3-24 chars)kv-salesapp-prod-eastus-01 (key vaults: global uniqueness)Use Azure Policy to enforce tags like
Owner,Environment,CostCenter, andCriticality.Continuously audit tag compliance using Azure Policy compliance dashboards.
Pro tip: Document your naming and tagging standard in the internal wiki - and make it mandatory for all deployments, including IaC.
Key Takeaways: Governance Is a Living Framework
Governance isn’t a one-time setup. It’s a living framework that evolves as your Azure footprint grows.
The strongest enterprises treat governance as the foundation, not an afterthought.
If you’re starting your Azure journey - or cleaning up an inherited environment - begin here:
Define your management structure early.
Lock down access and roles with least privilege.
Enforce policy and tagging standards automatically.
Build cost transparency into every subscription.
Review and adapt governance quarterly - not annually.
Final Thoughts
Azure governance failures aren’t due to technology gaps - they’re process and discipline gaps.
As architects, our job is to build cloud environments that are not only functional, but controlled, compliant, and cost-efficient.
If your governance feels reactive or fragmented today, don’t wait for an audit or budget escalation to fix it. Start small, automate, and scale your governance framework deliberately.
Because in Azure, good governance isn’t overhead - it’s protection.
If you found this useful, tap Subscribe at the bottom of the page to get future updates straight to your inbox.